Companies run many different websites for their business. To access any hostname, you require a unique IP address. Now we all know buying public IP addresses is not affordable always and is also not a feasible solution due to the shortage of IP addresses. To address this concern enters the Server Name Indication technology aka SNI technology.
SNI is a technology that allows hosting of multiple websites (hostnames) on the same public IP address, without the exclusive need of procuring IP address for individual hosts. It is an extension of the TLS protocol. It indicates which hostname is being contacted by the browser at the beginning of the handshake process.
Also read
How to protect IP addresses with SSL Certificate?
Let me give you some simple examples here to help you understand how SNI works. A server hosting many different websites on the same IP address is like an apartment providing a house to 10 different families. To access a specific family a visitor needs to know the proper house number and a respective floor as well.
SNI is like an example above, a server can host many TLS/SSL-enabled websites on the same public IP addresses. To access a specific website the client (browser) needs to specify which site they want to communicate during the initial handshake process.
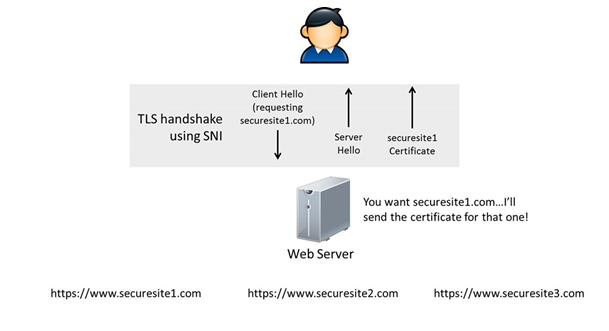
Refer to the below, an SNI enabled server will send a hostname as a parameter to initiate a TLS handshake process. This will allow the server to pass the request to the right website. Without SNI a server will not be able to address the right request generated by a client.
ESNI stands for encrypted SNI. The client encrypts the SNI even though the rest of the ClientHello message is sent in plaintext. The server publishes a public key on a well-known DNS record, which can be fetched by the client before connecting. The client then replaces the SNI extension in the ClientHello with an “encrypted SNI” extension, which is none other than the original SNI extension, but encrypted using a shared encryption key derived using the server’s public key. The server, which owns the private key and can derive the shared key as well, can then decrypt the extension and therefore terminate the connection. Since only the client, and the server to which it is connecting to, can derive the encryption key, the encrypted SNI cannot be decrypted and sniffed by third parties.
Different types of servers require different types of steps to enable SNI. You can get in touch with us and we can help you enable it on the server.
